Update wiki and add new articles
parent
3b35987ee2
commit
e79a65d47b
|
|
@ -0,0 +1,22 @@
|
|||
# Comparing AdGuard Home to other solutions
|
||||
|
||||
## How is this different from public AdGuard DNS servers?
|
||||
|
||||
Running your own AdGuard Home server allows you to do much more than using a public DNS server.
|
||||
|
||||
* Choose what exactly will the server block or not block.
|
||||
* Monitor your network activity.
|
||||
* Add your own custom filtering rules.
|
||||
* TODO: Most importantly, this is your own server, and you are the only one who is in control.
|
||||
|
||||
In the future, AdGuard Home is supposed to become more than just a DNS server.
|
||||
|
||||
## How does AdGuard Home compare to Pi-Hole
|
||||
|
||||
TBD
|
||||
|
||||
## How does AdGuard Home compare to traditional ad blockers
|
||||
|
||||
TBD
|
||||
|
||||
It depends. "DNS blackholing" is capable of blocking a big chunk of ads, but it lacks flexibility and power of the traditional ad blocking. A good example is [this article](https://adguard.com/en/blog/adguard-vs-adaway-dns66/) that compares `AdGuard for Android` with hosts-level ad blockers. However, this level of protection is enough for some users.
|
||||
|
|
@ -0,0 +1,80 @@
|
|||
# AdGuard Home - Configuration
|
||||
|
||||
Most of these settings can be changed via the web-based admin interface. However, we decided to list them all here just in case.
|
||||
|
||||
## Command-line arguments
|
||||
|
||||
Here is a list of all available command-line arguments.
|
||||
|
||||
```
|
||||
$ ./AdGuardHome --help
|
||||
Usage:
|
||||
|
||||
./AdGuardHome [options]
|
||||
|
||||
Options:
|
||||
-c, --config path to the config file
|
||||
-w, --work-dir path to the working directory
|
||||
-h, --host host address to bind HTTP server on
|
||||
-p, --port port to serve HTTP pages on
|
||||
-s, --service service control action: status, install, uninstall, start, stop, restart
|
||||
-l, --logfile path to the log file. If empty, writes to stdout, if 'syslog' -- system log
|
||||
-v, --verbose enable verbose output
|
||||
--help print this help
|
||||
```
|
||||
|
||||
Please note, that the command-line arguments override settings from the configuration file.
|
||||
|
||||
## Configuration file
|
||||
|
||||
Upon the first execution, a file named `AdGuardHome.yaml` will be created, with default values written in it. You can modify the file while your AdGuard Home service is not running. Otherwise, any changes to the file will be lost because the running program will overwrite them.
|
||||
|
||||
Settings are stored in [YAML format](https://en.wikipedia.org/wiki/YAML), possible parameters that you can configure are listed below:
|
||||
|
||||
* `bind_host` — Web interface IP address to listen on.
|
||||
* `bind_port` — Web interface IP port to listen on.
|
||||
* `auth_name` — Web interface optional authorization username.
|
||||
* `auth_pass` — Web interface optional authorization password.
|
||||
* `dns` — DNS configuration section.
|
||||
* `bind_host` - DNS interface IP address to listen on.
|
||||
* `port` — DNS server port to listen on.
|
||||
* `protection_enabled` — Whether any kind of filtering and protection should be done, when off it works as a plain dns forwarder.
|
||||
* `filtering_enabled` — Filtering of DNS requests based on filter lists.
|
||||
* `blocked_response_ttl` — For how many seconds the clients should cache a filtered response. Low values are useful on LAN if you change filters very often, high values are useful to increase performance and save traffic.
|
||||
* `querylog_enabled` — Query logging (also used to calculate top 50 clients, blocked domains and requested domains for statistical purposes).
|
||||
* `ratelimit` — DDoS protection, specifies in how many packets per second a client should receive. Anything above that is silently dropped. To disable set 0, default is 20. Safe to disable if DNS server is not available from internet.
|
||||
* `ratelimit_whitelist` — If you want exclude some IP addresses from ratelimiting but keep ratelimiting on for others, put them here.
|
||||
* `refuse_any` — Another DDoS protection mechanism. Requests of type ANY are rarely needed, so refusing to serve them mitigates against attackers trying to use your DNS as a reflection. Safe to disable if DNS server is not available from internet.
|
||||
* `bootstrap_dns` — DNS server used for initial hostname resolution in case if upstream server name is a hostname.
|
||||
* `parental_sensitivity` — Age group for parental control-based filtering, must be either 3, 10, 13 or 17 if enabled.
|
||||
* `parental_enabled` — Parental control-based DNS requests filtering.
|
||||
* `safesearch_enabled` — Enforcing "Safe search" option for search engines, when possible.
|
||||
* `safebrowsing_enabled` — Filtering of DNS requests based on safebrowsing.
|
||||
* `upstream_dns` — List of upstream DNS servers.
|
||||
* `filters` — List of filters, each filter has the following values:
|
||||
* `enabled` — Current filter's status (enabled/disabled).
|
||||
* `url` — URL pointing to the filter contents (filtering rules).
|
||||
* `name` — Name of the filter. If it's an adguard syntax filter it will get updated automatically, otherwise it stays unchanged.
|
||||
* `last_updated` — Time when the filter was last updated from server.
|
||||
* `ID` - filter ID (must be unique).
|
||||
* `dhcp` - Built-in DHCP server configuration.
|
||||
* `enabled` - DHCP server status.
|
||||
* `interface_name` - network interface name (eth0, en0 and so on).
|
||||
* `gateway_ip` - gateway IP address.
|
||||
* `subnet_mask` - subnet mask.
|
||||
* `range_start` - start IP address of the controlled range.
|
||||
* `range_end` - end IP address of the controlled range.
|
||||
* `lease_duration` - lease duration in seconds. If 0, using default duration (2 hours).
|
||||
* `tls` - HTTPS/DOH/DOT settings.
|
||||
* `enabled` - encryption (DOT/DOH/HTTPS) status.
|
||||
* `server_name` - the hostname of your HTTPS/TLS server.
|
||||
* `force_https` - if true, forces HTTP->HTTPS redirect.
|
||||
* `port_https` - HTTPS port. If 0, HTTPS will be disabled.
|
||||
* `port_dns_over_tls` - DNS-over-TLS port. If 0, DOT will be disabled.
|
||||
* `certificate_chain` - PEM-encoded certificates chain.
|
||||
* `private_key` - PEM-encoded private key.
|
||||
* `user_rules` — User-specified filtering rules.
|
||||
* `log_file` — Path to the log file. If empty, writes to stdout, if `syslog` -- system log (or eventlog on Windows).
|
||||
* `verbose` — Enable our disables debug verbose output.
|
||||
|
||||
Removing an entry from settings file will reset it to the default value. Deleting the file will reset all settings to the default values.
|
||||
|
|
@ -0,0 +1,108 @@
|
|||
# AdGuard Home - Docker
|
||||
|
||||
|
||||
<p align="center">
|
||||
<img src="https://cdn.adguard.com/public/Adguard/Common/adguard_home.svg" width="300px" alt="AdGuard Home" />
|
||||
</p>
|
||||
<h3 align="center">Privacy protection center for you and your devices</h3>
|
||||
<p align="center">
|
||||
Free and open source, powerful network-wide ads & trackers blocking DNS server.
|
||||
</p>
|
||||
|
||||
<br />
|
||||
|
||||
<p align="center">
|
||||
<img src="https://cdn.adguard.com/public/Adguard/Common/adguard_home.gif" width="800" />
|
||||
</p>
|
||||
|
||||
AdGuard Home is a network-wide software for blocking ads & tracking. After you set it up, it'll cover ALL your home devices, and you don't need any client-side software for that.
|
||||
|
||||
## How does AdGuard Home work?
|
||||
|
||||
AdGuard Home operates as a DNS server that re-routes tracking domains to a "black hole," thus preventing your devices from connecting to those servers. It's based on software we use for our public [AdGuard DNS](https://adguard.com/en/adguard-dns/overview.html) servers -- both share a lot of common code.
|
||||
|
||||
## Supported tags / architectures
|
||||
|
||||
`adguard/adguardhome` image is built for different architectures and supports the following tags:
|
||||
|
||||
* `latest` - latest **stable** build from the last tagged release.
|
||||
* `edge` - latest build from the repository **master** trunk, may be unstable.
|
||||
* `$version` - specific release e.g. `v0.92`.
|
||||
|
||||
### Tags for different architectures
|
||||
|
||||
* **ARM64** - 64bit ARM build
|
||||
* `arm64-latest`
|
||||
* `arm64-edge`
|
||||
* **ARMHF** - 32bit ARM build
|
||||
* `armhf-latest`
|
||||
* `armhf-edge`
|
||||
* **i386** - x86 build
|
||||
* `i386-latest`
|
||||
* `i386-edge`
|
||||
* **AMD64** - x86_64 build **default**
|
||||
* `latest`
|
||||
* `edge`
|
||||
|
||||
## Usage
|
||||
|
||||
To run `AdGuardHome` image:
|
||||
|
||||
```bash
|
||||
docker run -d --net=host adguard/adguardhome
|
||||
```
|
||||
|
||||
Now open the browser and navigate to http://DOCKER_HOST_IP:3000/ to control your AdGuard Home service.
|
||||
|
||||
## Persistent configuration / data
|
||||
|
||||
There are several ways to store data used by applications that run in Docker containers.
|
||||
We encourage users of the `adguard/adguardhome` images to familiarize themselves with the options available, including:
|
||||
|
||||
* Let Docker manage the storage of data by writing the files to disk on the host system using its own internal volume management.
|
||||
This is the default and is easy and fairly transparent to the user.
|
||||
The downside is that the files may be hard to locate for tools and applications that run directly on the host system, i.e. outside containers.
|
||||
|
||||
* Create a data directory on the host system (outside the container) and mount this to a directory visible from inside the container.
|
||||
This places the files in a known location on the host system, and makes it easy for tools and applications on
|
||||
the host system to access the files. The downside is that the user needs to make sure that the directory exists, and
|
||||
that e.g. directory permissions and other security mechanisms on the host system are set up correctly.
|
||||
|
||||
The image exposes two volumes for data/configuration persistence:
|
||||
* Configuration - `/opt/adguardhome/conf`
|
||||
* Filters and data - `/opt/adguardhome/work`
|
||||
|
||||
The Docker documentation is a good starting point for understanding the different storage options and variations, and there are multiple blogs and forum postings that discuss and give advice in this area. We will simply show the basic procedure here for the latter option above:
|
||||
|
||||
Create a **data** directory on a suitable volume on your host system, e.g. **/my/own/workdir**.
|
||||
|
||||
Create a **config** directory on a suitable volume on your host system, e.g. **/my/own/confdir**.
|
||||
|
||||
Start your `adguard/adguardhome` container like this:
|
||||
|
||||
```
|
||||
docker run --name adguardhome -v /my/own/workdir:/opt/adguardhome/work -v /my/own/confdir:/opt/adguardhome/conf -d --net=host adguard/adguardhome
|
||||
```
|
||||
|
||||
The `-v /my/own/workdir:/opt/adguardhome/work` part of the command mounts the `/my/own/workdir` directory from the underlying host system as `/opt/adguardhome/work` inside the container,
|
||||
where AdGuardHome by default will write its data files.
|
||||
|
||||
### Additional configuration
|
||||
|
||||
Upon the first execution, a file named `AdGuardHome.yaml` will be created, with default values written in it.
|
||||
You can modify the file while your AdGuard Home container is not running.
|
||||
Otherwise, any changes to the file will be lost because the running program will overwrite them.
|
||||
|
||||
Settings are stored in [YAML format](https://en.wikipedia.org/wiki/YAML), possible parameters that you can configure are listed on [Project homepage](https://github.com/AdguardTeam/AdGuardHome).
|
||||
|
||||
## How to update
|
||||
|
||||
```bash
|
||||
docker pull adguard/adguardhome
|
||||
```
|
||||
|
||||
To update the image for a specific architecture e.g. `arm64`:
|
||||
|
||||
```bash
|
||||
docker pull adguard/adguardhome:arm64-latest
|
||||
```
|
||||
|
|
@ -0,0 +1,100 @@
|
|||
# AdGuard Home - Encryption
|
||||
|
||||
We are proud to say that AdGuard Home supports all modern DNS encryptions protocols **out-of-the-box**:
|
||||
|
||||
* [DNS-over-HTTPS](https://en.wikipedia.org/wiki/DNS_over_HTTPS)
|
||||
* [DNS-over-TLS](https://en.wikipedia.org/wiki/DNS_over_TLS)
|
||||
* [DNSCrypt](https://dnscrypt.info/) (upstreams only)
|
||||
|
||||
In this guide we will explain how to setup your own "Secure DNS" server with AdGuard Home.
|
||||
|
||||
1. [Install AdGuard Home on your server](#install)
|
||||
2. [Register a domain name](#register)
|
||||
3. [Get an SSL certificate](#certificate)
|
||||
* [Install CertBot](#certbot)
|
||||
* [Get a certificate using DNS challenge](#certbot-dnschallenge)
|
||||
4. [Configure AdGuard Home](#configure-home)
|
||||
5. [Configure your devices](#configure-devices)
|
||||
|
||||
<a id="install"></a>
|
||||
## Install AdGuard Home on your server
|
||||
|
||||
It does not make much sense to configure DNS encryption inside of your own local network. The purpose of securing your DNS traffic is to secure it from third-parties that might be analyzing or modifying it. For instance, from your ISP.
|
||||
|
||||
It means that you will need a server with a public dedicated IP address. There are plenty of cheap cloud servers providers: [DigitalOcean](https://digitalocean.com), [Vultr](https://vultr.com), [Linode](https://www.linode.com/). Just choose any of them, create a cloud server there, and [install AdGuard Home](Gettiing-Started) on your server.
|
||||
|
||||
<a id="register"></a>
|
||||
## Register a domain name
|
||||
|
||||
First of all, you need a domain name. If you have never done it, here is a [simple instruction](https://www.pcworld.com/article/241722/web-apps/how-to-register-your-own-domain-name.html) that will help you with that.
|
||||
|
||||
<a id="certificate"></a>
|
||||
## Get an SSL certificate
|
||||
|
||||
Both `DNS-over-HTTPS` and `DNS-over-TLS` are based on [TLS encryption](https://en.wikipedia.org/wiki/Transport_Layer_Security) so in order to use them, you will need to acquire an SSL certificate.
|
||||
|
||||
An SSL certificate can be bought from a "Certificate Authority" (CA), a company trusted by browsers and operating systems to enroll SSL certificates for domains.
|
||||
|
||||
Alternatively, you can get the certificate for free from ["Let's Encrypt" CA](https://letsencrypt.org/), a free certificate authority developed by the Internet Security Research Group (ISRG).
|
||||
|
||||
In this guide I'll explain how to get a certificate from them.
|
||||
|
||||
<a id="certbot"></a>
|
||||
### Install CertBot
|
||||
|
||||
Certbot is an easy-to-use client that fetches a certificate from Let’s Encrypt.
|
||||
|
||||
1. Go to [https://certbot.eff.org/](https://certbot.eff.org/) and choose "None of the above" software and your operating system.
|
||||
2. Follow the installation instructions, and stop there - don't get to the "Get Started" section.
|
||||
|
||||
<a id="certbot-dnschallenge"></a>
|
||||
### Get a certificate using DNS challenge
|
||||
|
||||
You have just got a domain name so I suppose using DNS challenge will be the easiest way to get a certificate.
|
||||
|
||||
Run this command and follow the certbot's instructions:
|
||||
```bash
|
||||
sudo certbot certonly --manual --preferred-challenges=dns
|
||||
```
|
||||
|
||||
In the end you'll get two files:
|
||||
* `fullchain.pem` -- your PEM-encoded SSL certificate
|
||||
* `privkey.pem` -- your PEM-encoded private key
|
||||
|
||||
Both will be necessary to configure AdGuard Home.
|
||||
|
||||
<a id="configure-home"></a>
|
||||
## Configure AdGuard Home
|
||||
|
||||
1. Open AdGuard Home web interface and go to settings.
|
||||
2. Scroll down to the "Encryption" settings
|
||||
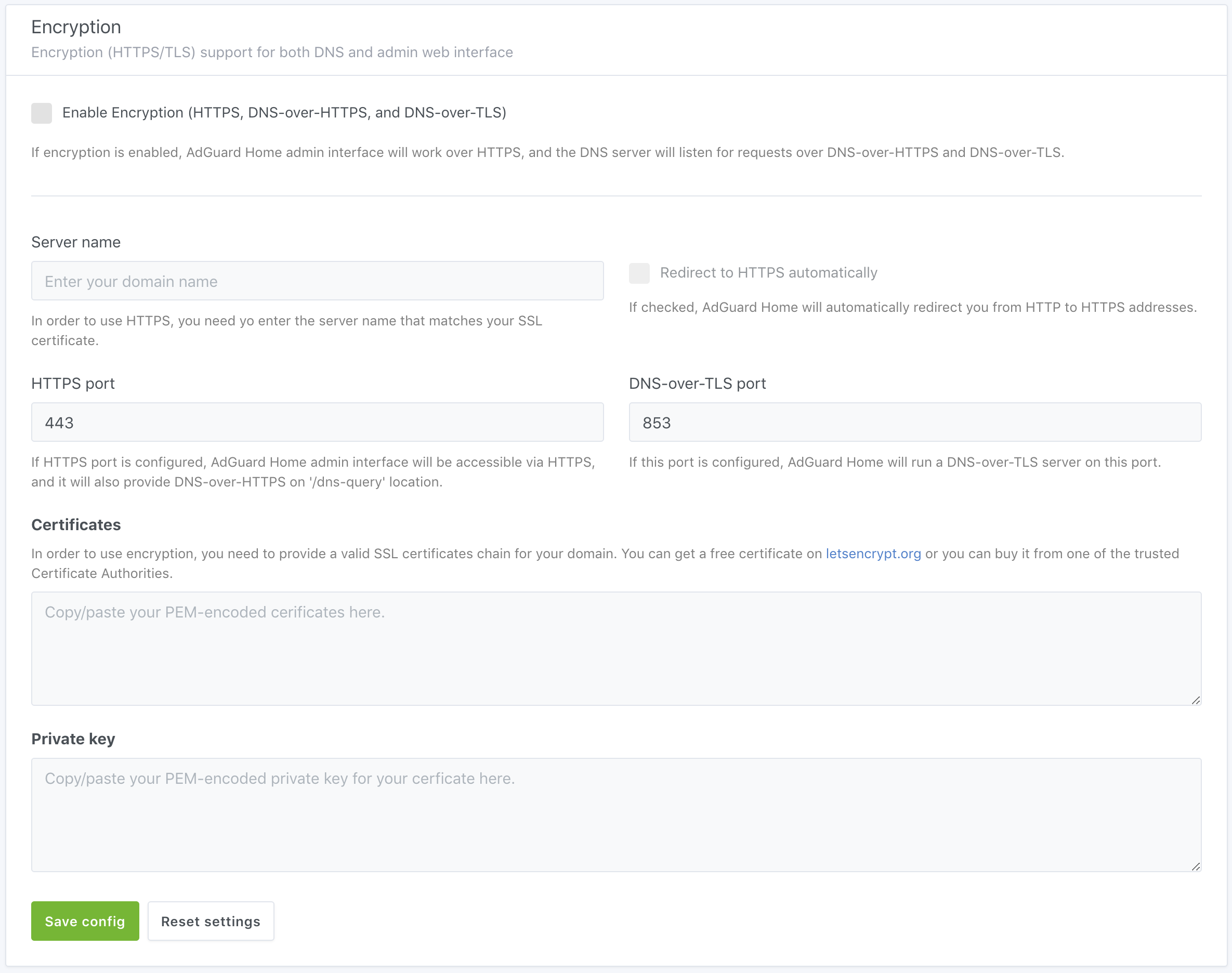
|
||||
3. Copy/paste the contents of the `fullchain.pem` file to "Certificates"
|
||||
4. Copy/paste the contents of the `privkey.pem` file to "Private key"
|
||||
5. Enter your domain name to "Server name"
|
||||
6. Click "Save settings".
|
||||
|
||||
<a id="configure-devices"></a>
|
||||
## Configure your devices
|
||||
|
||||
Please note that encrypted DNS protocols aren't supported at an operating system level (except Android 9) so right now it requires the installation of additional software.
|
||||
|
||||
Here's a list of the software that could be used.
|
||||
|
||||
### Android
|
||||
|
||||
* Android 9 supports DNS-over-TLS natively. To configure it, go to Settings → Network & internet → Advanced → Private DNS and enter your domain name there.
|
||||
* [AdGuard for Android](https://adguard.com/en/adguard-android/overview.html) supports `DNS-over-HTTPS` and `DNS-over-TLS` in the [beta update channel](https://adguard.com/beta.html).
|
||||
* [Intra](https://getintra.org/) adds `DNS-over-HTTPS` support to Android.
|
||||
|
||||
### iOS
|
||||
|
||||
* [DNSCloak](https://itunes.apple.com/app/id1452162351) supports `DNS-over-HTTPS` but in order to configure it to use your own server, you'll need to generate a [DNS Stamp](https://dnscrypt.info/stamps) for it.
|
||||
|
||||
### Other implementations
|
||||
|
||||
* AdGuard Home itself can be a secure DNS client on any platform.
|
||||
* [dnsproxy](https://github.com/AdguardTeam/dnsproxy) supports all known secure DNS protocols.
|
||||
* [dnscrypt-proxy](https://github.com/jedisct1/dnscrypt-proxy) supports `DNS-over-HTTPS`.
|
||||
* [Mozilla Firefox](https://www.mozilla.org/firefox/) supports `DNS-over-HTTPS`.
|
||||
* A lot more implementation can be [found here](https://dnscrypt.info/implementations) and [here](https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Clients).
|
||||
|
|
@ -0,0 +1,161 @@
|
|||
# AdGuard Home - Getting Started
|
||||
|
||||
In order to start using AdGuard Home, you need to do a few things:
|
||||
|
||||
1. [Installation](#installation)
|
||||
2. [Running for the first time](#first-time)
|
||||
3. [Running as a service](#service)
|
||||
4. [How to update](#update)
|
||||
5. [Configure your devices](#configure-devices)
|
||||
6. [Running without superuser (linux only)](#running-without-superuser)
|
||||
|
||||
<a id="installation"></a>
|
||||
## Installation
|
||||
|
||||
Download the archive with the binary file for your operating system from the [latest stable release](https://github.com/AdguardTeam/AdGuardHome/releases/latest).
|
||||
|
||||
We currently **officially** support the following operating systems:
|
||||
|
||||
* [MacOS](https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.92-hotfix2/AdGuardHome_v0.92-hotfix2_MacOS.zip)
|
||||
* [Windows 64-bit](https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.92-hotfix2/AdGuardHome_v0.92-hotfix2_Windows.zip)
|
||||
* [Linux 64-bit](https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.92-hotfix2/AdGuardHome_v0.92-hotfix2_linux_amd64.tar.gz)
|
||||
* [Linux 32-bit](https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.92-hotfix2/AdGuardHome_v0.92-hotfix2_linux_386.tar.gz)
|
||||
* [Rapsberry Pi (32-bit ARM)](https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.92-hotfix2/AdGuardHome_v0.92-hotfix2_linux_arm.tar.gz)
|
||||
|
||||
> AdGuard Home can work on other operating systems as well (for instance, it can work on devices with MIPS CPU), but we need your help with testing it.
|
||||
|
||||
<a id="first-time"></a>
|
||||
## Running for the first time
|
||||
|
||||
DNS works on port 53, which requires superuser privileges. Therefore, you need to run it with `sudo` in terminal:
|
||||
|
||||
```bash
|
||||
sudo ./AdGuardHome
|
||||
```
|
||||
|
||||
> On Windows, you will need to run `cmd.exe` with admin privileges and run `AdGuardHome.exe` from there.
|
||||
|
||||
When you run AdGuard Home for the first time, it will start listening to `0.0.0.0:3000` and prompt you to open it in your browser:
|
||||
|
||||
```
|
||||
AdGuard Home is available on the following addresses:
|
||||
Go to http://127.0.0.1:3000
|
||||
Go to http://X.X.X.X:3000
|
||||
```
|
||||
|
||||
There you will go through the initial configuration wizard.
|
||||
|
||||
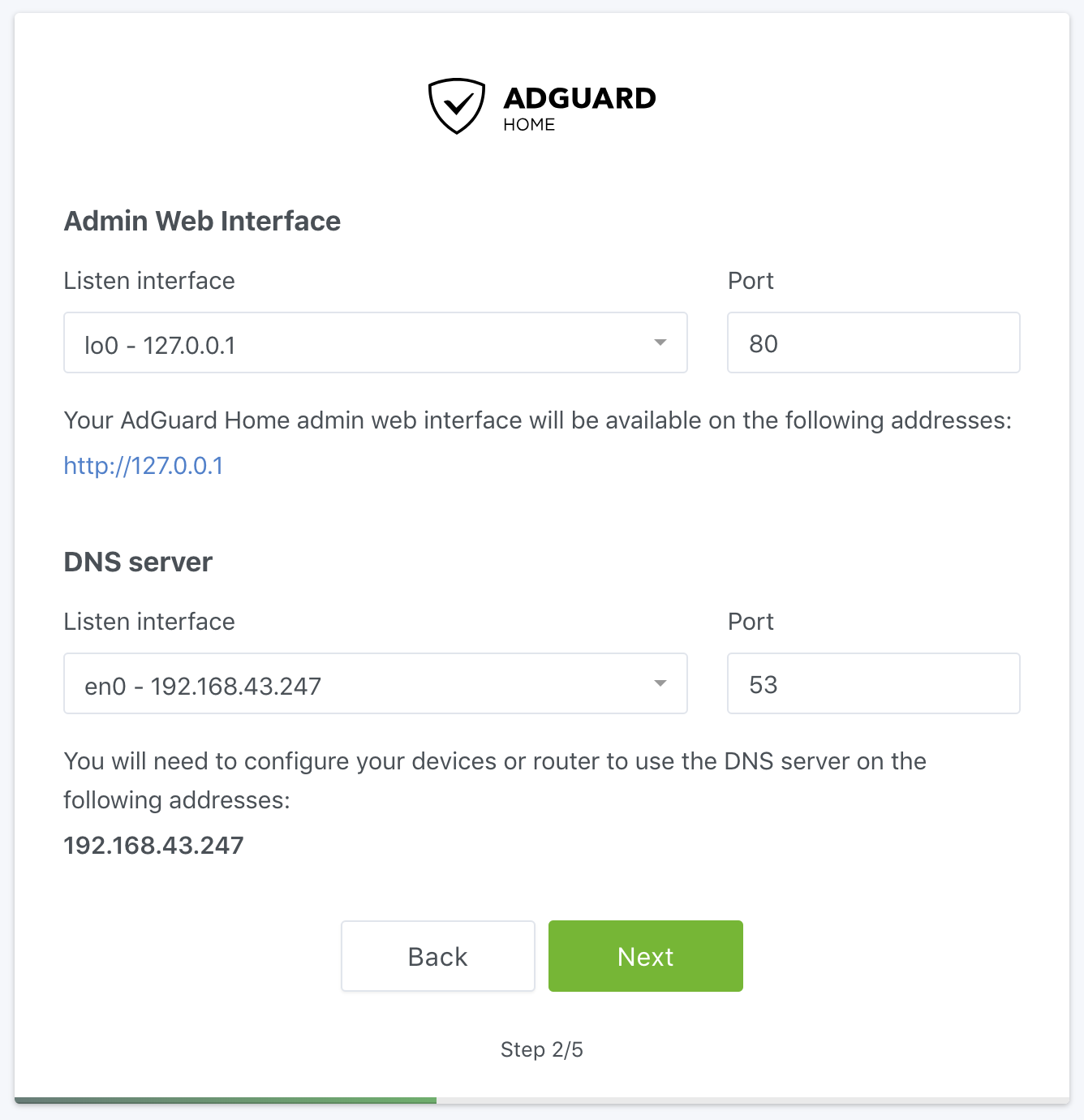
|
||||
|
||||
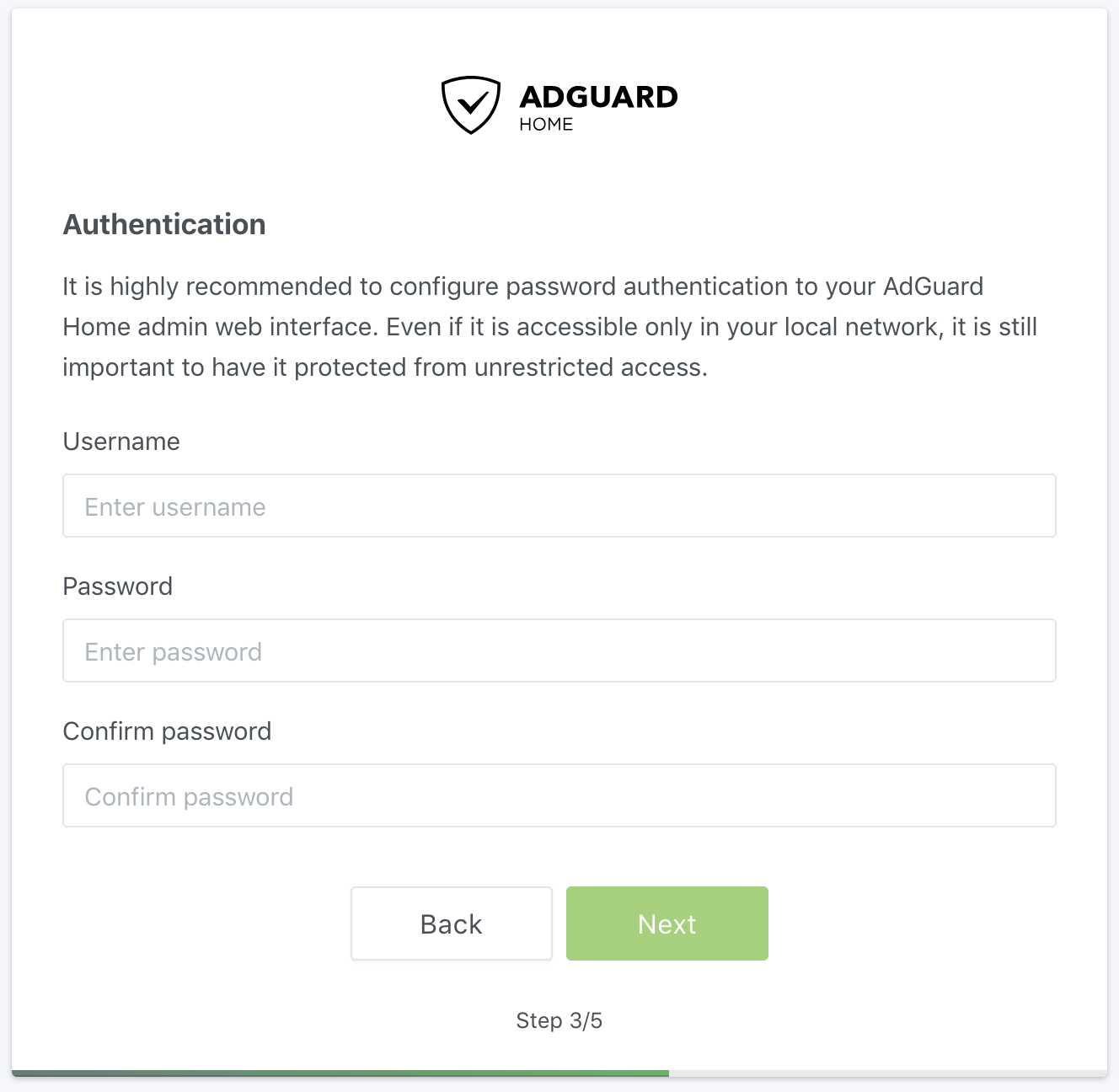
|
||||
|
||||
<a id="service"></a>
|
||||
## Running as a service
|
||||
|
||||
The next step would be to register AdGuard Home as a system service on Windows, Linux/(systemd | Upstart | SysV), or OSX/Launchd.
|
||||
|
||||
Run `sudo ./AdGuardHome -s install` to install AdGuard Home as a system service.
|
||||
|
||||
> On Windows run `cmd.exe` with admin privileges and run `AdGuardHome.exe -s install` to register a windows service.
|
||||
|
||||
Here are the other commands you might need to control the service.
|
||||
|
||||
* `AdGuardHome -s uninstall` - uninstalls the AdGuard Home service.
|
||||
* `AdGuardHome -s start` - starts the service.
|
||||
* `AdGuardHome -s stop` - stops the service.
|
||||
* `AdGuardHome -s restart` - restarts the service.
|
||||
* `AdGuardHome -s status` - shows the current service status.
|
||||
|
||||
> ### Logs
|
||||
> By default, the log is written to stderr when you run AdGuard Home as a console application.
|
||||
>
|
||||
> If you run it as a service/daemon, the log output depends on the platform:
|
||||
>
|
||||
> * Linux: the log is written to syslog.
|
||||
> * MacOS: the log is written to /var/log/AdGuardHome.*.log files.
|
||||
> * Windows: the log is written to the Windows event log.
|
||||
>
|
||||
> You can redefine this behavior in the AdGuard Home [configuration file](Configuration).
|
||||
|
||||
<a id="update"></a>
|
||||
## How to update
|
||||
|
||||
We have not yet implemented an auto-update of AdGuard Home, but it is planned for future versions.
|
||||
|
||||
At the moment, the update procedure is manual:
|
||||
|
||||
1. Download the new AdGuard Home binary.
|
||||
2. Replace the old file with the new one.
|
||||
3. Restart AdGuard Home.
|
||||
|
||||
<a id="configure-devices"></a>
|
||||
## How to configure your devices
|
||||
|
||||
### Router
|
||||
|
||||
This setup will automatically cover all the devices connected to your home router, and you will not need to configure each of them manually.
|
||||
|
||||
1. Open the preferences for your router. Usually, you can access it from your browser via a URL (like http://192.168.0.1/ or http://192.168.1.1/). You may be asked to enter the password. If you don’t remember it, you can often reset the password by pressing a button on the router itself. Some routers require a specific application, which in that case should be already installed on your computer/phone.
|
||||
2. Find the DHCP/DNS settings. Look for the ’DNS’ letters next to a field which allows two or three sets of numbers, each broken into four groups of one to three digits.
|
||||
3. Enter your AdGuard Home server addresses there.
|
||||
|
||||
### Android
|
||||
|
||||
1. From the Android Menu home screen, tap ’Settings’
|
||||
2. Tap Wi-Fi on the menu. This will show a list of all of the available networks (it is impossible to set custom DNS for mobile connection)
|
||||
3. Long press the network you’re connected to, and tap ’Modify Network’
|
||||
4. On some devices, you may need to check the box for ’Advanced’ to see further settings. To adjust your Android DNS settings, you will need to switch the IP settings from ’DHCP’ to ’Static.’
|
||||
5. Change ’DNS 1′ and ’DNS 2′ values to your AdGuard Home address.
|
||||
|
||||
### iOS
|
||||
|
||||
1. From the home screen, tap ’Settings’
|
||||
2. Choose ’Wi-Fi’ in the left menu (it is impossible to configure DNS for mobile networks)
|
||||
3. Tap on the name of the currently active network
|
||||
4. In the ’DNS’ field enter your AdGuard Home address
|
||||
|
||||
### macOS
|
||||
|
||||
1. Click on Apple icon and go to ’System Preferences.’
|
||||
2. Click on ’Network’
|
||||
3. Select the first connection in your list and click ’Advanced.’
|
||||
4. Select the ’DNS’ tab and add the address of your AdGuard Home.
|
||||
|
||||
### Windows
|
||||
|
||||
1. Open Control Panel through ’Start’ menu or Windows search.
|
||||
2. Go to ’Network and Internet’ category and then to ’Network and Sharing Center.’
|
||||
3. On the left side of the screen find ’Change adapter settings’ and click on it.
|
||||
4. Select your active connection, right-click on it and choose ’Properties.’
|
||||
5. Find ’Internet Protocol Version 4 (TCP/IP)’ in the list, select it and then click on ’Properties’ again.
|
||||
5. Choose ’Use the following DNS server addresses’ and enter your AdGuard Home address there.
|
||||
|
||||
<a id="running-without-superuser"></a>
|
||||
## Running without superuser (linux only)
|
||||
|
||||
You can run AdGuard Home without superuser privileges, but you need to either grant the binary a capability (on Linux) or instruct it to use a different port (all platforms).
|
||||
|
||||
#### Granting the CAP_NET_BIND_SERVICE capability (on Linux)
|
||||
|
||||
Note: using this method requires the `setcap` utility. You may need to install it using your Linux distribution's package manager.
|
||||
|
||||
To allow AdGuard Home running on Linux to listen on port 53 without superuser privileges, run:
|
||||
|
||||
```bash
|
||||
sudo setcap CAP_NET_BIND_SERVICE=+eip ./AdGuardHome
|
||||
```
|
||||
|
||||
Then run `./AdGuardHome` as a unprivileged user.
|
||||
|
||||
#### Changing the DNS listen port
|
||||
|
||||
To configure AdGuard Home to listen on a port that does not require superuser privileges, edit `AdGuardHome.yaml` and find these two lines:
|
||||
|
||||
```yaml
|
||||
dns:
|
||||
port: 53
|
||||
```
|
||||
|
||||
You can change port 53 to anything above 1024 to avoid requiring superuser privileges.
|
||||
|
||||
If the file does not exist, create it in the same folder, type these two lines down and save.
|
||||
85
Home.md
85
Home.md
|
|
@ -1,65 +1,32 @@
|
|||
# AdGuard Home - Wiki
|
||||
|
||||
|
||||
<p align="center">
|
||||
<img src="https://cdn.adguard.com/public/Adguard/Common/adguard_home.svg" width="300px" alt="AdGuard Home" />
|
||||
</p>
|
||||
<h3 align="center">Privacy protection center for you and your devices</h3>
|
||||
<p align="center">
|
||||
Free and open source, powerful network-wide ads & trackers blocking DNS server.
|
||||
</p>
|
||||
|
||||
<br />
|
||||
|
||||
<p align="center">
|
||||
<img src="https://cdn.adguard.com/public/Adguard/Common/adguard_home.gif" width="800" />
|
||||
</p>
|
||||
|
||||
<hr />
|
||||
|
||||
Welcome to the AdGuard Home wiki!
|
||||
|
||||
The wiki was just recently created, so there isn't much content (yet).
|
||||
|
||||
## FAQ
|
||||
|
||||
### What is AdGuard Home and why do you need it?
|
||||
|
||||
AdGuard Home is a network-wide software for blocking ads & tracking. After you set it up, it'll cover ALL your home devices, and you don't need any client-side software for that. With the rise of Internet-Of-Things and connected devices, it becomes more and more important to be able to control your whole network.
|
||||
|
||||
> Please note, that the current state of AdGuard Home is just the beginning. Configuring it requires some technical skills, and we'll try to simplify the process in the future.
|
||||
|
||||
## How does it work?
|
||||
|
||||
AdGuard Home operates as a DNS server that re-routes tracking domains to a "black hole," thus preventing your devices from connecting to those servers. It's based on software we use for our public [AdGuard DNS](https://adguard.com/en/adguard-dns/overview.html) servers -- both share a lot of common code.
|
||||
|
||||
## How to install AdGuard Home?
|
||||
## Guides
|
||||
|
||||
* [Getting Started](Getting-Started)
|
||||
* [AdGuard Home Docker](Docker)
|
||||
* [Configuration](Configuration)
|
||||
* [Comparing AdGuard Home to other solutions](Comparison)
|
||||
* [AdGuard Home as a DNS-over-HTTPS or DNS-over-TLS server](Encryption)
|
||||
* [How to install and run AdGuard Home on Raspberry Pi](Raspberry-Pi)
|
||||
* [How to install and run AdGuard Home on a Virtual Private Server](VPS)
|
||||
|
||||
## How do I set up my devices to use my AdGuard Home?
|
||||
|
||||
### Router
|
||||
|
||||
This setup will automatically cover all the devices connected to your home router, and you will not need to configure each of them manually.
|
||||
|
||||
1. Open the preferences for your router. Usually, you can access it from your browser via a URL (like http://192.168.0.1/ or http://192.168.1.1/). You may be asked to enter the password. If you don’t remember it, you can often reset the password by pressing a button on the router itself. Some routers require a specific application, which in that case should be already installed on your computer/phone.
|
||||
2. Find the DHCP/DNS settings. Look for the ’DNS’ letters next to a field which allows two or three sets of numbers, each broken into four groups of one to three digits.
|
||||
3. Enter your AdGuard Home server addresses there.
|
||||
|
||||
### Android
|
||||
|
||||
1. From the Android Menu home screen, tap ’Settings’
|
||||
2. Tap Wi-Fi on the menu. This will show a list of all of the available networks (it is impossible to set custom DNS for mobile connection)
|
||||
3. Long press the network you’re connected to, and tap ’Modify Network’
|
||||
4. On some devices, you may need to check the box for ’Advanced’ to see further settings. To adjust your Android DNS settings, you will need to switch the IP settings from ’DHCP’ to ’Static.’
|
||||
5. Change ’DNS 1′ and ’DNS 2′ values to your AdGuard Home address.
|
||||
|
||||
### iOS
|
||||
|
||||
1. From the home screen, tap ’Settings’
|
||||
2. Choose ’Wi-Fi’ in the left menu (it is impossible to configure DNS for mobile networks)
|
||||
3. Tap on the name of the currently active network
|
||||
4. In the ’DNS’ field enter your AdGuard Home address
|
||||
|
||||
### macOS
|
||||
|
||||
1. Click on Apple icon and go to ’System Preferences.’
|
||||
2. Click on ’Network’
|
||||
3. Select the first connection in your list and click ’Advanced.’
|
||||
4. Select the ’DNS’ tab and add the address of your AdGuard Home.
|
||||
|
||||
### Windows
|
||||
|
||||
1. Open Control Panel through ’Start’ menu or Windows search
|
||||
2. Go to ’Network and Internet’ category and then to ’Network and Sharing Center.’
|
||||
3. On the left side of the screen find ’Change adapter settings’ and click on it
|
||||
4. Select your active connection, right-click on it and choose ’Properties.’
|
||||
5. Find ’Internet Protocol Version 4 (TCP/IP)’ in the list, select it and then click on ’Properties’ again
|
||||
5. Choose ’Use the following DNS server addresses’ and enter your AdGuard Home address there
|
||||
|
||||
## Can I throw out traditional ad blockers now?
|
||||
|
||||
It depends. "DNS blackholing" is capable of blocking a big chunk of ads, but it lacks flexibility and power of the traditional ad blocking. A good example is [this article](https://adguard.com/en/blog/adguard-vs-adaway-dns66/) that compares `AdGuard for Android` with hosts-level ad blockers. However, this level of protection is enough for some users.
|
||||
* [How to install and run AdGuard Home on a Virtual Private Server](VPS)
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
## Guides
|
||||
|
||||
* [Getting Started](Getting-Started)
|
||||
* [AdGuard Home Docker](Docker)
|
||||
* [Configuration](Configuration)
|
||||
* [Comparing AdGuard Home to other solutions](Comparison)
|
||||
* [AdGuard Home as a DNS-over-HTTPS or DNS-over-TLS server](Encryption)
|
||||
* [How to install and run AdGuard Home on Raspberry Pi](Raspberry-Pi)
|
||||
* [How to install and run AdGuard Home on a Virtual Private Server](VPS)
|
||||
Loading…
Reference in New Issue